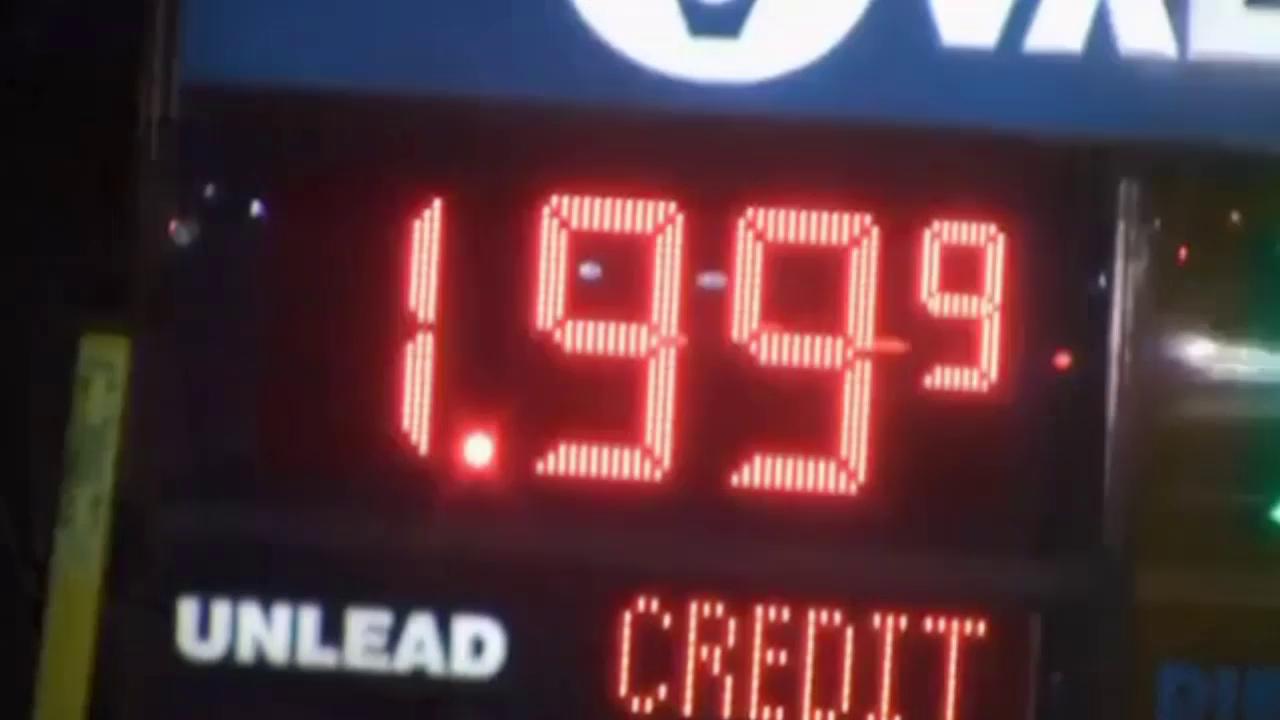Friday, January 30, 2015
Friday Forum: Mickey Mouse & the Measles
The above headlines represent the growing concern over the recent measles outbreak in the United States. Based on the headlines above, brainstorm at least five questions you have about this topic.
9 Things Everyone Should Know About Measles
Ebola was Only a Warmup: The Measles Outbreak is for Real
Parents who oppose measles vaccine, hold firm to their beliefs
Mom: Family that refused vaccination put my baby in quarantine
Thursday, January 29, 2015
The Costs of Cyber Crime
Cyber crime is one of the fastest growing criminal activities, and one of its most costliest. Today, we are going to look at the escalating financial harm caused by cyber crime, including the categories of theft and what countries suffer the most.
To begin, answer these three questions (take a guess!):
1. How much do officials estimate cyber crimes to cost worldwide?
2. What three countries report the greatest financial loss due to cyber crimes?
3. Name three types of economic cyber crime.
4. What country is believed to be the worst perpetrator of cyber economic espionage?
Articles
Estimated Cost of Cyber Crimes Worldwide
US Government Going After Hackers
To begin, answer these three questions (take a guess!):
1. How much do officials estimate cyber crimes to cost worldwide?
2. What three countries report the greatest financial loss due to cyber crimes?
3. Name three types of economic cyber crime.
4. What country is believed to be the worst perpetrator of cyber economic espionage?
Articles
Estimated Cost of Cyber Crimes Worldwide
US Government Going After Hackers
Wednesday, January 28, 2015
Cyber crimes
In addition to cyber warfare, another 21st century concern is cyber crime. Millions of people have already been affected by stolen data including Social Security numbers, credit card information, and bank account information. This growing field of criminal behavior is difficult to trace and transcends national boundaries, making law enforcement difficult.
What happens when you swipe your card?
One of the more well publicized cyber crimes involved the theft of credit card data from Target. Read about it here: Target breach shows you can be a victim of cybercrime at a brick and mortar store.
Tuesday, January 27, 2015
Presidential Power & Cyber Military Power
As the US builds up its cyber military capabilities, there are several questions about its use. First, what limitations are there on presidential power and use of cyber attacks? Should the US use the cyber military for defensive or offensive attacks?
Broad Powers Seen for Obama in Cyber Attacks
The Dangers of Obama's Cyber War Power Grab
Pentagon Goes on the Offensive Against Cyberattacks
Read the above articles and come up with several discussion questions for each article.
Broad Powers Seen for Obama in Cyber Attacks
The Dangers of Obama's Cyber War Power Grab
Pentagon Goes on the Offensive Against Cyberattacks
Read the above articles and come up with several discussion questions for each article.
Friday, January 23, 2015
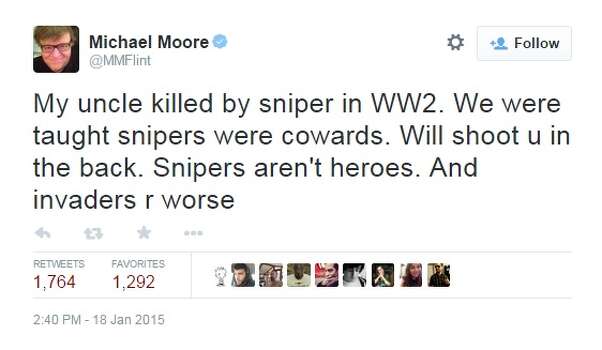
Friday Forum: American Sniper--Hero or Killer?
The movie American Sniper was released last week to record breaking ticket sales and critical acclaim. However, this Oscar nominated film has also raised some controversy over its portrayal of Chris Kyle, credited with the most sniper kills in US military history, as an American hero. Critics contend that it glorifies killing and is equivalent to American war propaganda.
American Sniper: Was Chris Kyle really a hero?
American Sniper: Was Chris Kyle really a hero?
Thursday, January 22, 2015
USCYBERCOM: The US Cyberspace Military
Army Cyber Protection Team
Assignment: Read the following article and answer the questions below.
First Strike: US Cyber Warriors Seize the Offensive
1. The Department of Defense has recently stated that cyberspace is the fifth domain, joining air, sea, land, and space. How is "cyber superiority" as critical in future conflicts as air superiority? What is the US military doing to achieve this advantage?
2. Explain what the zero-day market is. What is actually be sold? Who is competing to buy this information and why? What are some of the potential concerns?
3. Should private companies be legally allowed to strike back if information has been stolen or is it now a law enforcement or government responsibility? Explain your answer.
4. Has Stuxnet created a cyber arms race? Should there be an international treaty restricting the use of cyber weapons, similar to treaties on nuclear and chemical/biological weapons?
Tuesday, January 20, 2015
Cyber armies: Preparing for the next war?
Many experts believe that the next war will involve both conventional warfare and cyber warfare. Countries throughout the world are investing heavily in defensive and offensive capabilities. Today we are going to look several countries' cyber military capabilities.
Your task: Research your assigned country and find out as much as you can about their cyber military program. Prepare a briefing to present to the President of the United States.
Here are a few things you should try to find out:
Your task: Research your assigned country and find out as much as you can about their cyber military program. Prepare a briefing to present to the President of the United States.
Here are a few things you should try to find out:
- Name of program
- Size of program
- Budget
- When established
- Level of organization/acknowledgement by the government
- Recruitment/Training
- Suspected or known operations
- Defensive vs. Offensive
- Threat assessment
- Any other pertinent information
Countries: Iran, India, Russia, China, Israel, Syria, United Kingdom
Friday, January 16, 2015
What's Causing the Price of Gas to Drop?
Over the last several months, the price of gas has decreased dramatically. In many states (including Missouri), it is below $2 a gallon for the first time in several years. Today we'll take a look at the reasons for the drop in prices as well as the benefits.
Why oil prices keep falling--and throwing the world into turmoil
What the huge drop in gasoline prices means for America
Cheaper gas prices benefit some, hurt others
The unintended consequences of cheap oil
OPEC members feeling the pain of falling oil numbers
Questions:
1. List three reasons why oil prices (and gas prices as a result) continue to decline.
2. What businesses and industries are benefiting from this decrease in oil prices?
3. The decline in oil prices is not good news for everyone. Who is being negatively affected by the decrease?
4. What other negative consequences might we see from the drop in oil prices?
5. Should the US increase its gasoline tax?
Thursday, January 15, 2015
Bureau 121: The North Korean Cyber Army
As a result of the alleged hacking of the Sony Pictures computer systems, more attention has been paid to the North Korean cyber specialists, sometimes referred to as the Bureau 121. Many countries, including the United States, have invested heavily in training soldiers in cyber warfare, both for defensive and offensive purposes. North Korea has been expanding its cyber warfare program as tensions with South Korea and the United States continue.
Computer networks in South Korea are paralyzed in cyber attacks
In North Korea, hackers are a handpicked, pampered elite
North Korea doubles size of cyber army
Why cyber armies are a good investment for countries like North Korea
Computer networks in South Korea are paralyzed in cyber attacks
In North Korea, hackers are a handpicked, pampered elite
North Korea doubles size of cyber army
Why cyber armies are a good investment for countries like North Korea
Wednesday, January 14, 2015
More Cybervandalism: The Hacking of Sony
Late last year, Sony Pictures' computers were hacked and countless files were stolen. This attack made major headlines and many people think the infiltration was retaliation for Sony's movie, The Interview.
Research and read about this act of cybervandalism and answer the following questions. Please record your answers on a google doc and share with me (kgates@liberty.k12.mo.us)
1. What kind of damage was caused by this hack? What did the hackers find or release?
2. Who is considered behind the attacks? What evidence, if any, is there to link them to the attacks?
3. How is the movie, The Interview, involved in all of this? Should Sony have stopped the release of the movie?
4. What is the US government's response to this act? Do you think it is appropriate?
5. Do you think this cyber attack is a big deal? Why or why not?
The Sony Hack Explained
What Happened with the Sony Hack
Obama: Sony Attack was Cybervandalism, not an Act of War
US Slaps North Korea with New Sanctions
Sony insider--not North Korea--likely involved in the attack claim experts
North Korea: Show Us the Evidence
Research and read about this act of cybervandalism and answer the following questions. Please record your answers on a google doc and share with me (kgates@liberty.k12.mo.us)
1. What kind of damage was caused by this hack? What did the hackers find or release?
2. Who is considered behind the attacks? What evidence, if any, is there to link them to the attacks?
3. How is the movie, The Interview, involved in all of this? Should Sony have stopped the release of the movie?
4. What is the US government's response to this act? Do you think it is appropriate?
5. Do you think this cyber attack is a big deal? Why or why not?
The Sony Hack Explained
What Happened with the Sony Hack
Obama: Sony Attack was Cybervandalism, not an Act of War
US Slaps North Korea with New Sanctions
Sony insider--not North Korea--likely involved in the attack claim experts
North Korea: Show Us the Evidence
Tuesday, January 13, 2015
Centcom Social Media Hacked
CNN: CENTCOM Twitter account hacked, suspended
U.S. military social media accounts apparently hacked by Islamic State sympathizers
The real reason pro-ISIS hackers took over CENTCOM's Twitter
Assignment:
1) Find two other examples of "cybervandalism" by the Cyber Caliphate and summarize their actions.
2) On a scale of 1-10, how serious of a threat or how concerned should we be by these acts? Explain.
Assignment:
1) Find two other examples of "cybervandalism" by the Cyber Caliphate and summarize their actions.
2) On a scale of 1-10, how serious of a threat or how concerned should we be by these acts? Explain.
Monday, January 12, 2015
Stuxnet
Stuxnet is a computer worm that was discovered in 2010 and is considered to be the world's first real digital weapon. Targeting Iran's nuclear program and disrupting its centrifuges, this complex code is believed to be a joint operation between the United States and Israel.
60 Minutes: Stuxnet Computer Worm Opens Up New Era of Warfare
How did they crack the code and discover Stuxnet's intended target?
From Bullets to Megabytes
Why is Stuxnet so important?
60 Minutes: Stuxnet Computer Worm Opens Up New Era of Warfare
How did they crack the code and discover Stuxnet's intended target?
From Bullets to Megabytes
Why is Stuxnet so important?
Ralph Langner, the German computer security specialist credited with discovering Stuxnet, says it doesn't matter who created Duqu. The problem, he says, is that Stuxnet, in its bid to stop nuclear proliferation, may have sparked its own arms race.
"The first cyberwar weapon is comparable to the first nuclear weapon," he wrote in a blog post recently. "To build the first nuclear bomb, it took a genius like Oppenheimer and the resources of the Manhattan project. To copy the design, it requires just a bunch of engineers -- no genius needed.
(Source: http://www.cnn.com/2011/11/08/tech/iran-stuxnet/)
Discussion Questions:
1. Is Stuxnet an illegal act of cyber warfare?
2. Has Stuxnet created a cyber warfare arms race?
3. How could a similar virus be used against the United States?
4. Was the use of Stuxnet a good idea? Did its ability to slow down Iran's nuclear program outweigh the potential copying of the program by others?
4. Was the use of Stuxnet a good idea? Did its ability to slow down Iran's nuclear program outweigh the potential copying of the program by others?
Thursday, January 8, 2015
The Charlie Hibdo Attack
Charlie Hebdo, a French satirical newspaper, was attacked by terrorists on Wednesday, resulting in twelve deaths and a nationwide manhunt for the perpetrators. What caused such anger and violence toward a group of middle-aged cartoonists? The weekly newspaper is well-known for its mocking of political and religious figures and anti-establishment views. It particularly skewers extremists from all areas of life, but Muslim extremists have taken great offense at the newspaper's depictions of Islam in general, and specifically its portrayal of Mohammed.
Read the following articles for more information:
1) Charlie Hebdo Attack: What We Know So Far
2) This is not the first time that depictions of Mohammed have caused violence. Read this Washington Post article for more instances.
3) On of the journalists/cartoonists in the above mentioned article, has been in hiding for the past few years because of death threats against her.
4) 12 Powerful Political Cartoons Responding to the Charlie Hibdo Attack
5) Many see this attack as not just an attack on the Charlie Hibdo newspaper, but an attack on freedom of speech itself.
Discussion Questions:
- Did Charlie Hibdo cross the line with its constant blasphemous depictions of Mohammed?
- Would the reactions be the same if a pro-white supremacy magazine was attacked for its racist depictions of African Americans or Jews?
- "I disapprove of what you say, but I will defend to the death your right to say it." Do you agree with this statement? Why or why not?
- What impact does this terrorist attack and the recent efforts to stop the release of the Sony movie, "The Interview" have on the freedom of speech, freedom of the press, and censorship? Do you think it will cause journalists, cartoonists, and other artists to be more cautious in their treatment of certain subjects?
Defining Cyber warfare
Is cyber warfare an act of war? Espionage? Terrorism? How do we define cyber warfare? Does it make a difference if it is committed by a nation-state, a group, or an individual? Does it matter on what the actual goal of the act is?
Define cyber warfare. What should the consequences be for an act of cyber warfare?
Please read the following article:
When is a cyberattack an act of war?
What should the government response be in each of the following scenarios?
1. A cyberattack by a sovereign nation that takes down a city power grid.
2. A virus disables an airplane control tower that results in two planes crashing and killing over 500 passengers. The virus is traced back to a computer server in Pakistan.
3. A group of computer hackers based in France steals millions of Americans' credit card information.
4. A cyberattack temporarily (15 minutes) disables our missile defense system. The attack is traced back to China.
5. A cyberattack hits Wall Street causing chaos and results in over $100 billion in losses.
Define cyber warfare. What should the consequences be for an act of cyber warfare?
Please read the following article:
When is a cyberattack an act of war?
What should the government response be in each of the following scenarios?
1. A cyberattack by a sovereign nation that takes down a city power grid.
2. A virus disables an airplane control tower that results in two planes crashing and killing over 500 passengers. The virus is traced back to a computer server in Pakistan.
3. A group of computer hackers based in France steals millions of Americans' credit card information.
4. A cyberattack temporarily (15 minutes) disables our missile defense system. The attack is traced back to China.
5. A cyberattack hits Wall Street causing chaos and results in over $100 billion in losses.
Wednesday, January 7, 2015
Thinking From a Different Perspective
One of the goals of this course is to help facilitate your ability to look at things from multiple perspectives and consider alternative solutions.
Sometimes what you see is not what other people see.
Sometimes the answer is not always obvious.

Sometimes we have to think carefully before we speak.
Sometimes when we look at things from a different perspective we see things we didn't see before.
How does thinking from a different perspective impact our study of different topics (i.e. Ferguson, the Middle East, etc.)?
Sometimes what you see is not what other people see.
Old Woman or Young Woman?
Native American profile or Inuit?
Duck or Rabbit?
Man playing a saxophone or a woman's face?
Six cubes or seven cubes?

Sometimes what seems like an easy solution or obvious answer does not quite work out that way upon closer examination.
Sometimes we have to think carefully before we speak.
Sometimes we have to read carefully. Sometimes we have to read a passage multiple times to really understand it.
Sometimes the big picture changes when we really focus on a specific area.
Sometimes the big picture changes when we really focus on a specific area.
Sometimes when we look at things from a different perspective we see things we didn't see before.
How does thinking from a different perspective impact our study of different topics (i.e. Ferguson, the Middle East, etc.)?
Tuesday, January 6, 2015
Welcome!
Course Description: Contemporary Issues is a semester long class that will look at a variety of current day issues and problems. Throughout the course we will determine what topics to examine and approach each of these issues from multiple perspectives. We will be using many tools of social science inquiry including statistics, maps, original documents, political cartoons, and surveys. The use of technology will be heavily incorporated in this course. The goal of this course is not to tell you what to think, but to encourage you to think critically.
Course Outline: The course will be divided into five to six units of study, each lasting approximately 3 weeks. The first unit will be determined by the instructor. The next three or four units will be determined by the class, and the final unit will be a topic of your own personal choice that you will research and prepare a presentation on. A detailed list of potential unit topics will be provided.
Methodology: This course will be very reading intensive. Most readings will be online and will be completed either before class on your own time, or occasionally in-class time will be provided. Discussions are also integral to this course. Respectful, courteous, and substantive comments are expected.
Grading & Assessments: Grades will be determined by homework assignments, reaction papers, post-assessments (tests), and participation. The standard grading system will be used.
Expectations: The main expectations for this course are to be respectful, participate, and be prepared. If you follow these three expectations, we should not have any problems.
Technology: As indicated, technology will be heavily incorporated into this course. Laptops will be used on a daily basis with readings, research, writing, collaboration, and creating. This will be a learning process for all of us. My goal is to have a virtually paperless class with all assignments, readings, projects, etc. delivered electronically. You will find most, if not all, information on this blog. Please make sure you are using technology in an appropriate manner and are on task.
Please create a Contemporary Issues folder on your bookmarks bar to keep links, articles, this page, etc.
Course Outline: The course will be divided into five to six units of study, each lasting approximately 3 weeks. The first unit will be determined by the instructor. The next three or four units will be determined by the class, and the final unit will be a topic of your own personal choice that you will research and prepare a presentation on. A detailed list of potential unit topics will be provided.
Methodology: This course will be very reading intensive. Most readings will be online and will be completed either before class on your own time, or occasionally in-class time will be provided. Discussions are also integral to this course. Respectful, courteous, and substantive comments are expected.
Grading & Assessments: Grades will be determined by homework assignments, reaction papers, post-assessments (tests), and participation. The standard grading system will be used.
Expectations: The main expectations for this course are to be respectful, participate, and be prepared. If you follow these three expectations, we should not have any problems.
Technology: As indicated, technology will be heavily incorporated into this course. Laptops will be used on a daily basis with readings, research, writing, collaboration, and creating. This will be a learning process for all of us. My goal is to have a virtually paperless class with all assignments, readings, projects, etc. delivered electronically. You will find most, if not all, information on this blog. Please make sure you are using technology in an appropriate manner and are on task.
Please create a Contemporary Issues folder on your bookmarks bar to keep links, articles, this page, etc.
Your first assignment:
Take three minutes and brainstorm possible broad topic areas (ex. military, health) you would like to learn more about through this course. Minimum of five.
In a group of 3-4 students, share and compare your answers.
Next, as a group, choose three of the broad topics and brainstorm possible subtopics to examine more closely in class (ex. Military/Use of drones, Health/Obesity)
Subscribe to:
Comments (Atom)